trooper (thm)
January 22nd 2025 | #ctf #cti #tryhackme
Task: "Use Cyber Threat Intelligence knowledge and skills to identify a threat based on a report."
What kind of phishing campaign does APT X use as part of their TTPs?
Answer: Spear-phishing emails
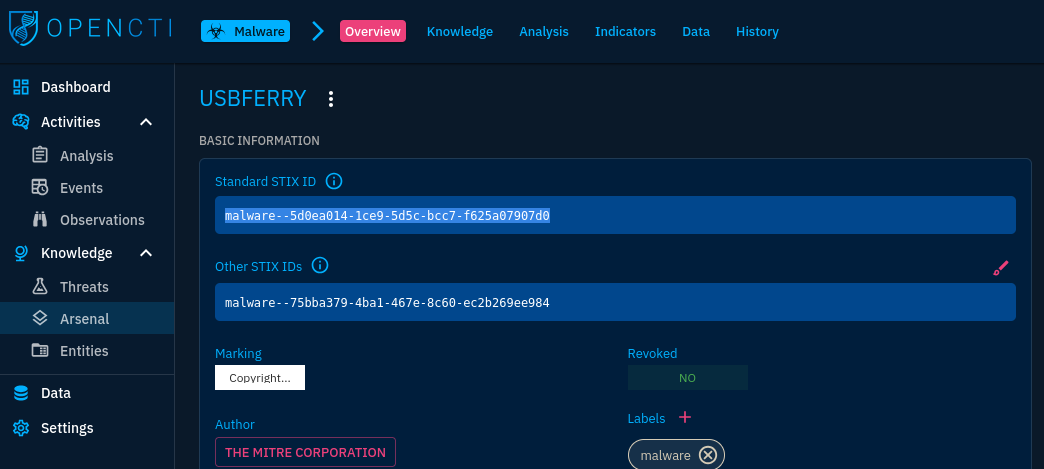
What is the name of the malware used by APT X?
Answer: USBFerry
What is the malwares STIX ID?
Answer: malware--5d0ea014-1ce9-5d5c-bcc7-f625a07907d0
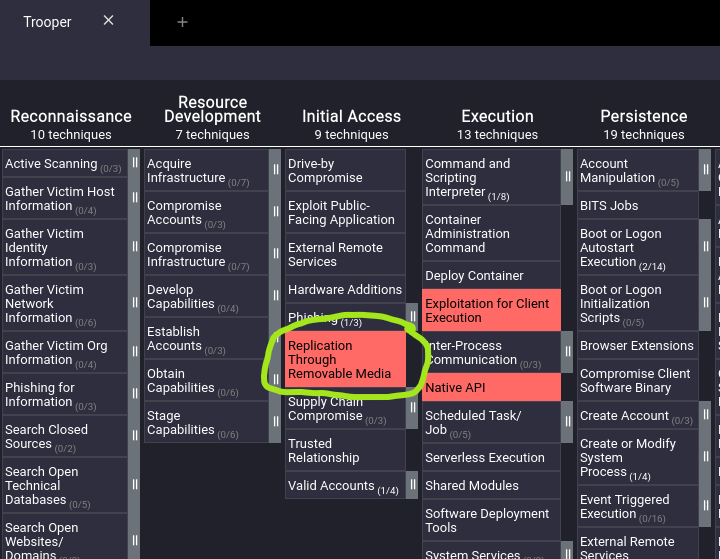
With the use of a USB, what technique did APT X use for initial access?
Answer: Replication Through Removable Media https://attack.mitre.org/techniques/T1091/
What is the identity of APT X?
Tropic Trooper is an unaffiliated threat group that has led targeted campaigns against targets in Taiwan, the Philippines, and Hong Kong. Tropic Trooper focuses on targeting government, healthcare, transportation, and high-tech industries and has been active since 2011.
Associated Groups: Pirate Panda, KeyBoy
Answer: Tropic Trooper
On OpenCTI, how many Attack Pattern techniques are associated with the APT?
Answer: 39
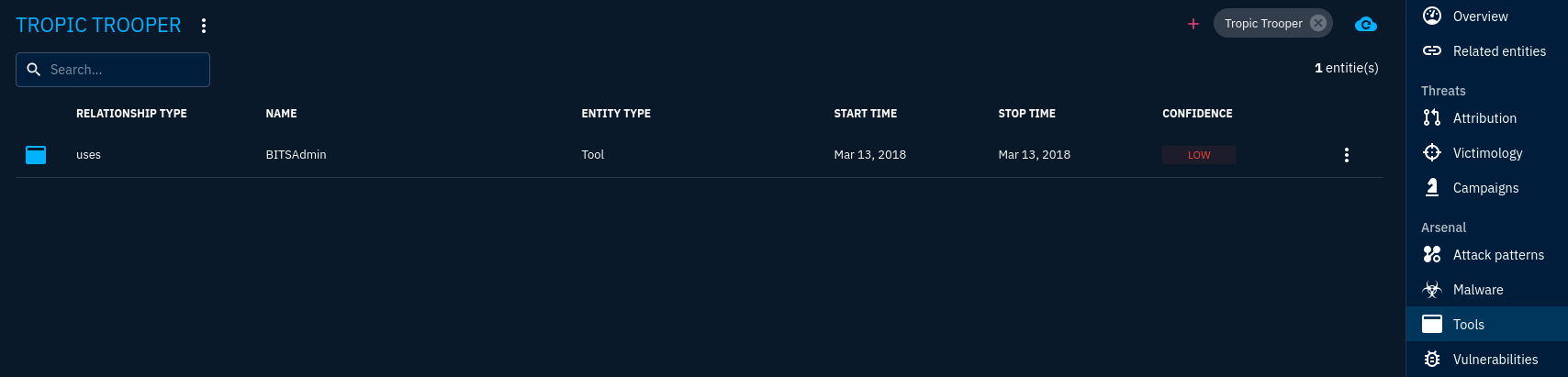
What is the name of the tool linked to the APT?
BITSAdmin is a command line tool used to create and manage BITS Jobs.
Answer: BITSAdmin
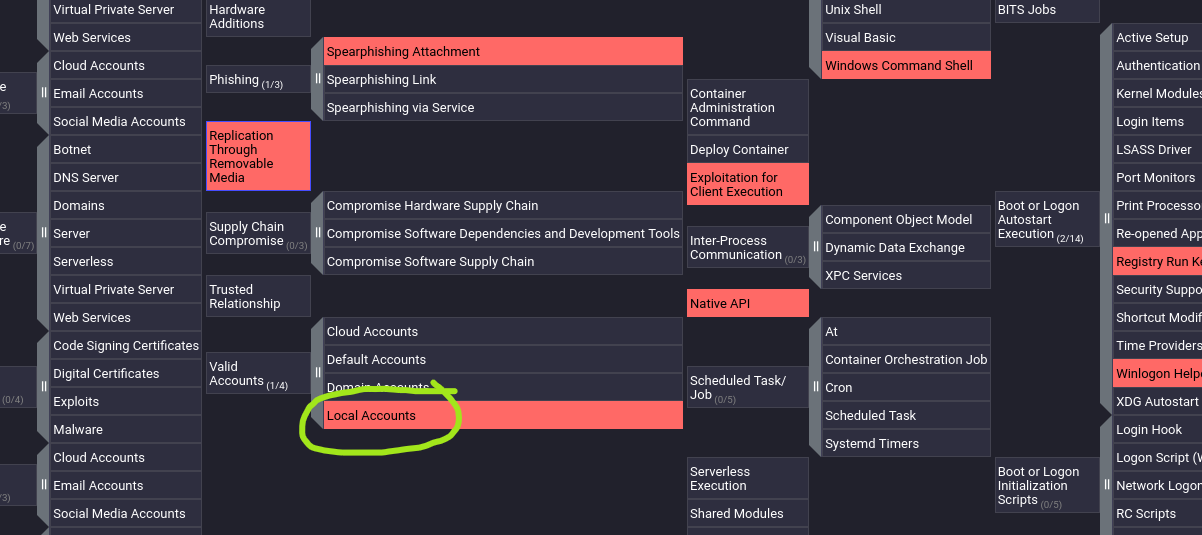
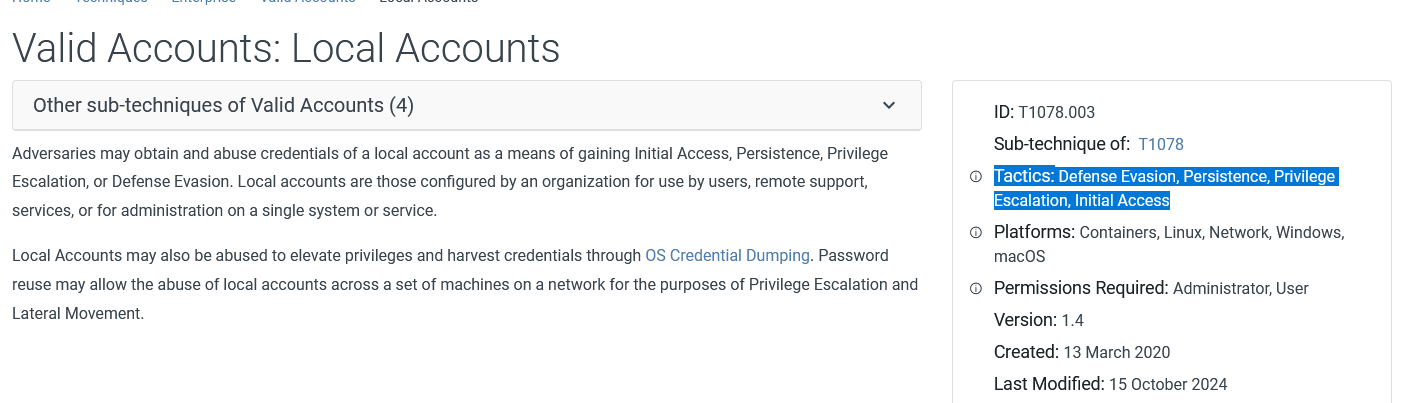
Load up the Navigator. What is the sub-technique used by the APT under Valid Accounts?
ID: T1078.003 Sub-technique of: T1078
Adversaries may obtain and abuse credentials of a local account as a means of gaining Initial Access, Persistence, Privilege Escalation, or Defense Evasion. Local accounts are those configured by an organization for use by users, remote support, services, or for administration on a single system or service.
Answer: Local Accounts
Under what Tactics does the technique above fall?
What technique is the group known for using under the tactic Collection?
Once established within a system or network, an adversary may use automated techniques for collecting internal data. Methods for performing this technique could include use of a Command and Scripting Interpreter to search for and copy information fitting set criteria such as file type, location, or name at specific time intervals.
https://attack.mitre.org/techniques/T1119/
Answer: Automated Collection
< The Killer Clown (hacktoria) | TryHack3M: Bricks Heist (thm) >