Investigation SOC235 - Atlassian Confluence Broken Access Control 0-day
I have been out of the SOC almost a year now and sometimes I miss digging into alerts. I recently signed up to letsdefend.io to play around. LetsDefend is a really cool training site with a simulated SOC environment that allows you to investigate incidents. The alerts are quite close to what you'd see in the real world. Read on for my analysis of alert SOC235.
Alert Details
⭐ CVE-2023-22515 affects certain versions of Atlassian Confluence Data Center and Server, enabling malicious cyber threat actors to obtain initial access to Confluence instances by creating unauthorized access
EventID: 197
Event Time: Nov, 08, 2023, 09:47 AM
Rule: SOC235 - Atlassian Confluence Broken Access Control 0-Day CVE-2023-22515
Level: Security Analyst
Hostname: Confluence Data Center
Destination IP Address: 172.16.17.234
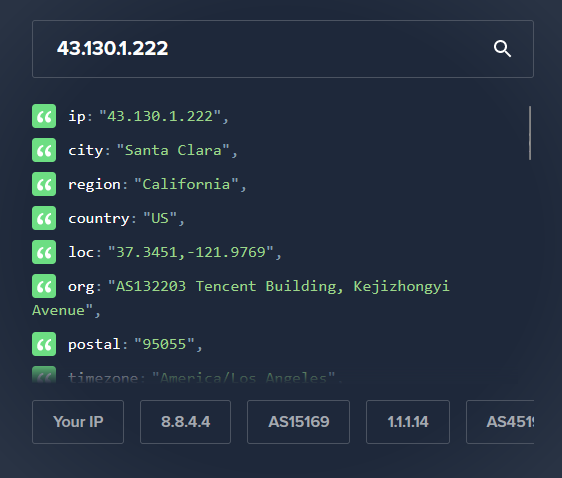
Source IP Address: 43.130.1.222
HTTP Request Method: GET
Requested URL: /server-info.action?bootstrapStatusProvider.applicationConfig.setupComplete=false
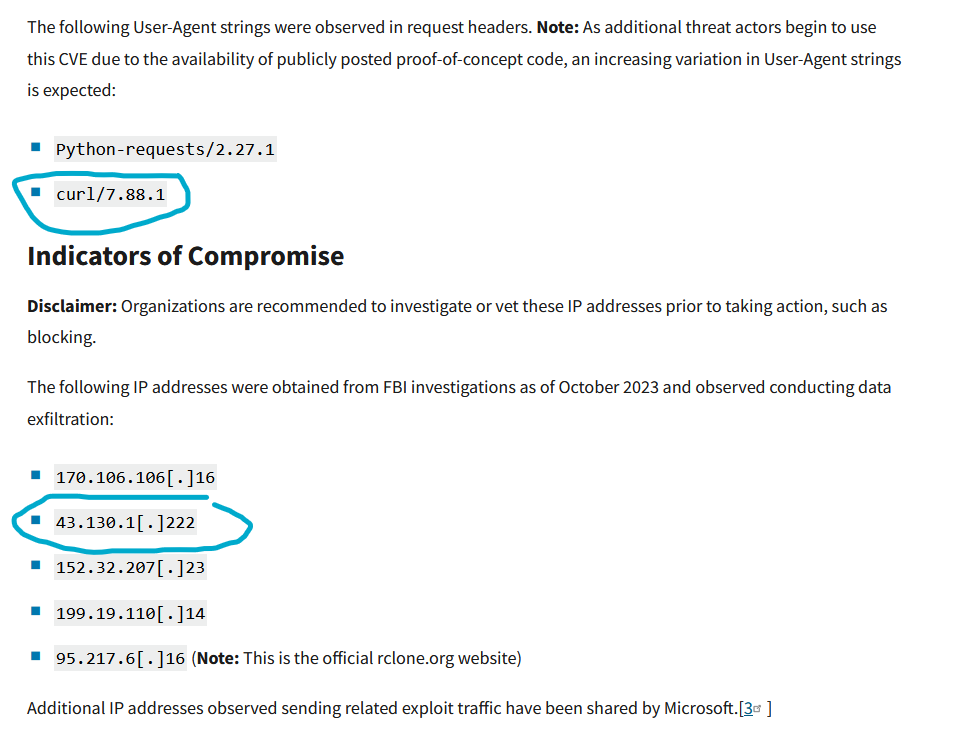
User-Agent: curl/7.88.1
Alert Trigger Reason: This activity may be indicative of an attempt to exploit the CVE-2023-22515 vulnerability, which could potentially lead to create a new administrator user.
Device Action: Allowed
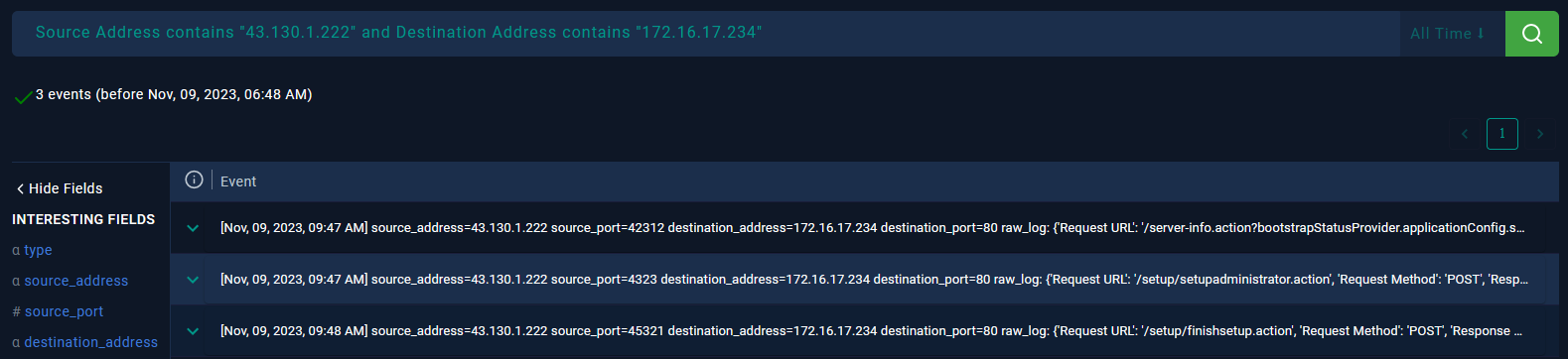
The traffic logs show three suspicious connections. The alert was triggered by one of the requests:
Victim Details
Hostname: Confluence Data Center v8.0.3
Domain: LetsDefend
IP Address: 172.16.17.234
Bit Level: 64
OS: Windows Server 2019
Primary User: LetsDefend
Client/Server: Server
Last Login: Nov, 08, 2023, 12:00 PM
Investigation
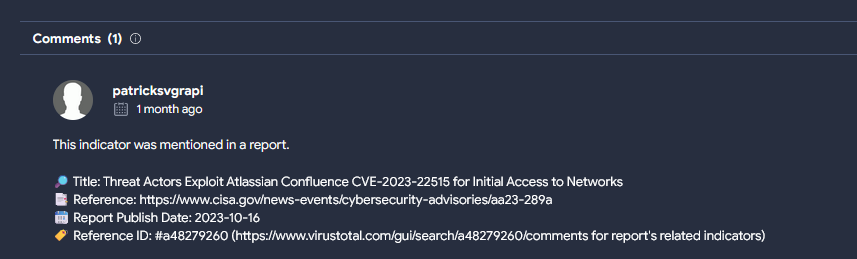
The alert refers to vulnerability CVE-2023-22515. A previously unknown vulnerability in publicly accessible Confluence Data Center and Server instances to create unauthorized Confluence administrator accounts and access Confluence instances. According to CISA Advisory AA23-289A threat actors exploited CVE-2023-22515 as a zero-day to obtain access to victim systems and continue active exploitation post-patch. Atlassian has rated this vulnerability as critical; CISA, FBI, and MS-ISAC expect widespread, continued exploitation due to ease of exploitation.
Several indicators (IP, User-Agent, ...) from the report have also appeared in our logs.
After creating a case, the SOC playbook guides you through the investigation steps by asking the relevant questions:
Is Traffic Malicious? Yes. Traffic comes from a flagged IP address and uses a User-Agent mentioned in the CISA report. The IP address is part of Tencent Cloud IP Range. OTX lists the IP as malicious.
What Is The Attack Type? Other. (CWE-20: Improper Input Validation)
Is the malicious traffic caused by a planned test? No
What Is the Direction of Traffic? Internet > Company Network
Was the attack successful? Successful Attack. The machine has been contained. Threat Actor IP Address from CISA advisory discovered in network traffic.
< Detectados intentos de Phishing a Office 365 / Siguiendo el Hilo | La contraseña tiene que morir >